In cybersecurity, lateral movement refers to techniques used by attackers to move within a network after initially compromising a single system. This can include techniques such as using stolen credentials to access other systems, exploiting vulnerabilities in network infrastructure, and using remote administration tools. The goal of lateral movement is typically to gain access to….

Cybersecurity Tools: EDR vs MDR vs XDR
Let’s Clear Up Common Misconceptions About Cybersecurity Tools The intended audience of this blog includes business owners, executives, IT managers, IT engineers and those curiously interested in IT. We seek to provide you with the latest IT knowledge and insights from our behind-the-scenes experience. We provide this information to help you manage the specific costs and risks of IT in your business. In our world today, data is our most valuable resource. Your organization’s….

Advanticom Maintains ISO 27001 Certification for 6th Year
As September quickly approaches and schools are back in session for the fall semester, it’s a reminder that audit season for Advanticom’s ISO 27001 certification is quickly kicking into full gear. This fall, Advanticom will be completing our sixth full year of ISO audits and with the start of 2023 we will be kicking off….

Advanticom Completes Ownership Transition to Current Employees
Advanticom is excited to formally announce that a successful ownership transition was completed at the end of May. The acquisition from current owner Brian Conboy was executed by a group of Advanticom’s employees, which is what makes this story stand out when compared to the trend of local IT firms selling to private equity backed national Managed….
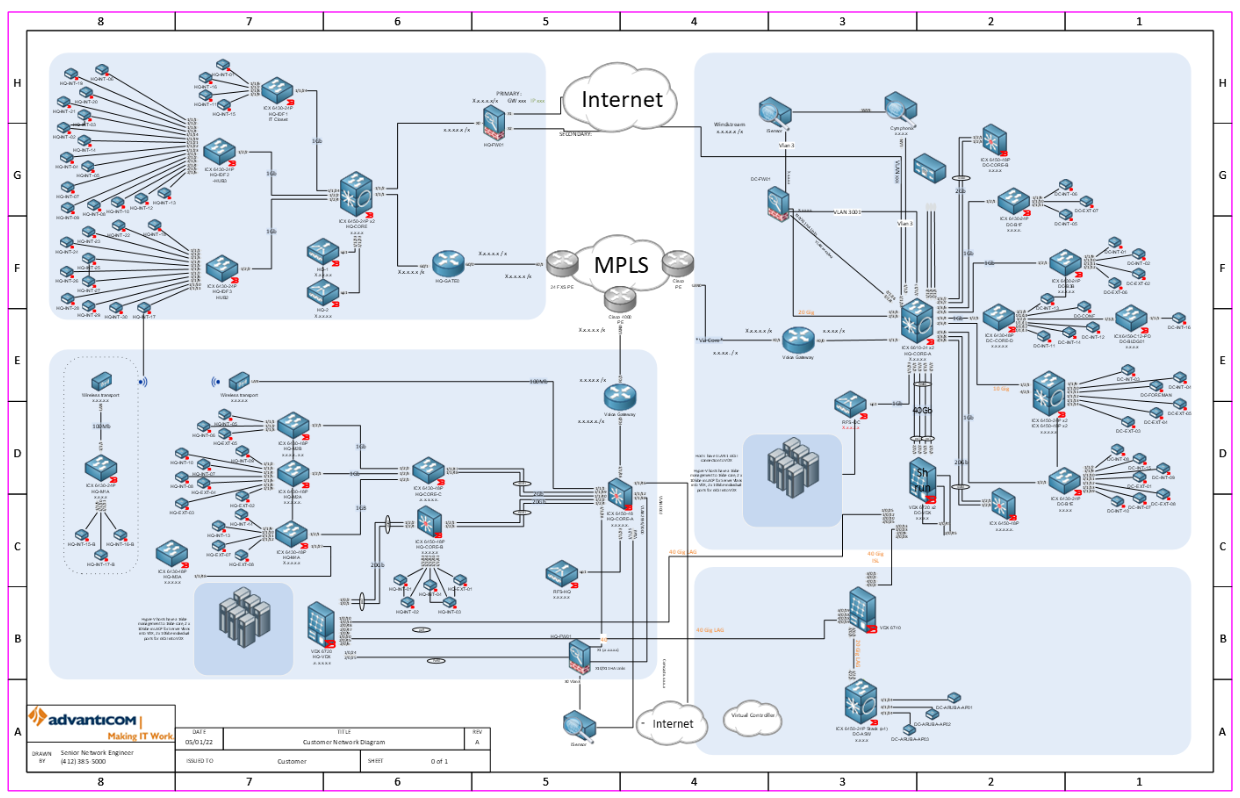
The Importance of Network Documentation
The intended audience of this blog includes business owners, executives, IT managers, IT engineers and those curiously interested in IT. We seek to provide you with the latest IT knowledge and insights from our behind-the-scenes experience. We provide this information to help you manage the specific costs and risks of IT in your business. You have heard it many times before: maintaining proper documentation is critical to your organization. It provides a….

