Every organization has countless passwords (keys) to access their corporate network. Each employee manages passwords for various systems like email, VPN, ERP, CRM, and HR. Executives and accountants often have even more to protect, accounting and financial systems, banking information, and maybe even proprietary data or trade secrets. Unfortunately, many companies have terrible password practices….
Maximize your Microsoft 365 and Microsoft Azure spend to reach your cloud potential with a Tier 1 Microsoft Cloud Solutions Provider (CSP)
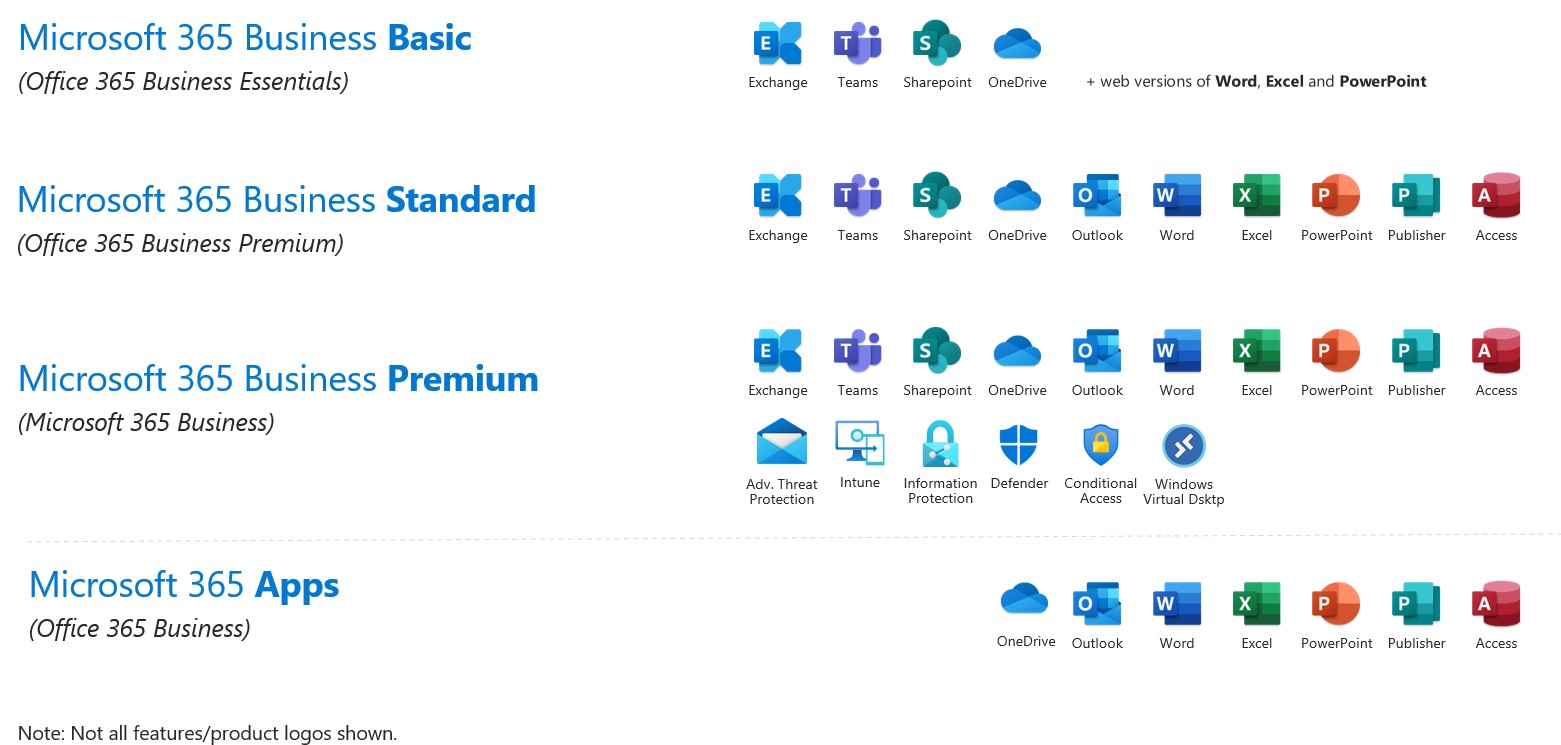
Navigating Microsoft 365 licensing can often be challenging. Microsoft releases new products, changes bundles, and adjusts promotions so often that it makes it difficult to track even for those trying to stay informed. To add slightly more confusion they also have a habit of changing names to existing products and bundles causing us all to….

The Critical Importance of Proper Asset and Inventory Management: Safeguarding Your Business Against Cyber Incidents
Often overlooked, IT asset and inventory management is crucial data for businesses to properly maintain. In an era where cyber threats are increasingly sophisticated and pervasive, the need for robust IT asset and inventory management has never been more critical. Effective asset management goes beyond mere record-keeping; it is a foundational practice that enhances security,….
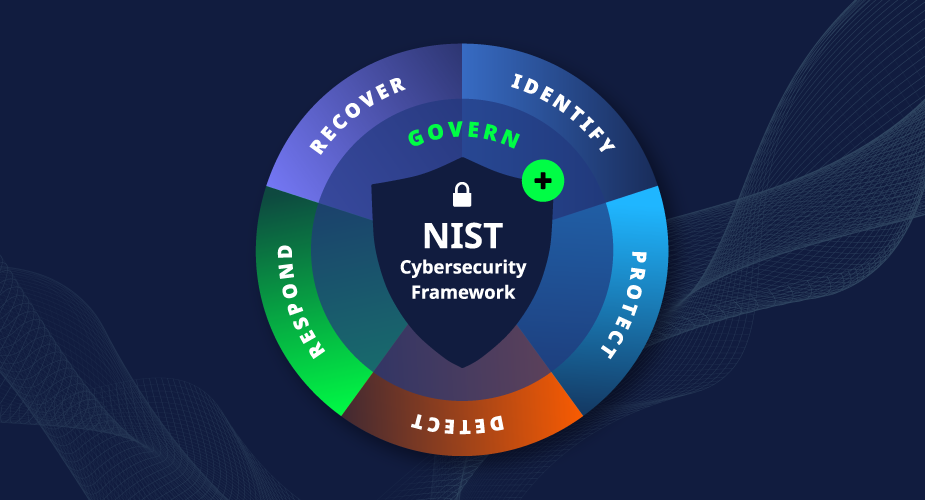
Improve Cyber Hygiene in 2024: Make A New Year’s Resolution to align with NIST Cybersecurity Framework
2024 is a great time for business owners and executives to be aware of the investments that the federal government has made to help businesses with cybersecurity best practice initiatives. For those not paying close attention there is a particular organization – the National Institute of Standards and Technology (NIST). NIST first produced their Cybersecurity….

The Evolving Threat of Hacking: Protecting Your Business in 2024
The Escalation of Cyber Attacks Over the past few years, the frequency and sophistication of cyber-attacks have escalated dramatically. Cybersecurity leaders acknowledge that cyberattacks are increasing and they expect prevalence of attempts to continue to increase over the foreseeable future. In the past 18-months there has been a staggering increase in phishing attacks reported with….

