As a business owner or executive, cybersecurity has become a considerable concern you have to pay attention to. The increasing efforts of cyber criminals need to be addressed within your organization to ensure you are mitigating risks and working to prevent a cyberattack. One particular area that demands attention is Supply Chain Attacks. Supply chain….

Building Resilience: The Importance of Business Continuity Planning
As the saying goes, “Hope for the best, but prepare for the worst.” That’s exactly what a business continuity plan (BCP) does – it helps organizations prepare for unexpected disruptions that could threaten their operations and profitability. While the idea of creating a BCP may seem daunting, the truth is that it’s an essential step….

Phishing Emails and Self Reporting
Phishing Attacks Are on the Rise Phishing attacks are increasing at a rapidly increasing rate and are becoming increasingly more difficult to discern from a legitimate email and the consequences for falling for them can be catastrophic. Phishing is a type of cybercrime that attempts to trick consumers into clicking a link or opening an….
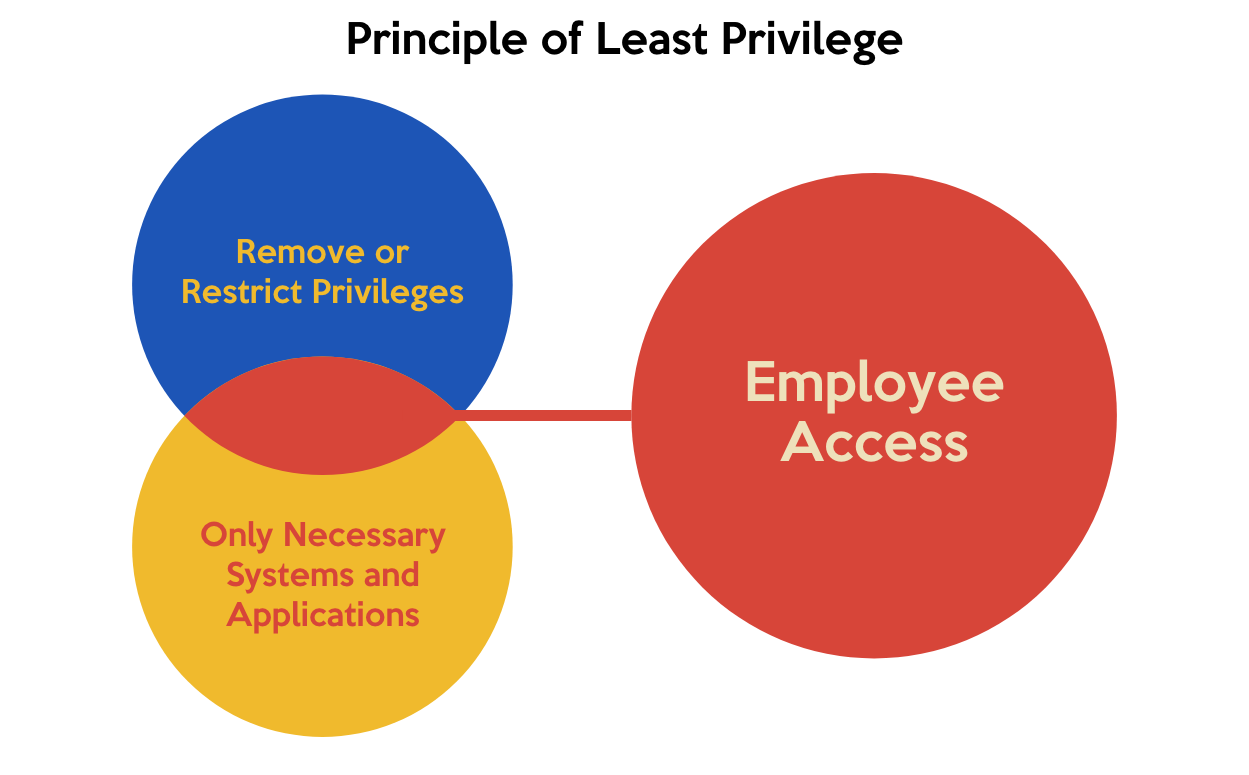
The Principle of Least Privilege
The principle of Least Privilege (POLP), also known as the principle of least authority or least access, is a security concept in computer systems and networks that limits the access rights of users and programs to the bare minimum necessary to perform their tasks. The principle of least privilege is considered a fundamental principle of….

USE IMMUTABLE BACKUP SERVICES TO DODGE RANSOMWARE WITH WORM STORAGE
Ransomware is a risk for all businesses. Ransomware is a type of malware that encrypts a victim’s files and demands a ransom payment to regain access. Many companies have paid the ransom, but unfortunately, even if the ransom is paid, there is no guarantee that the hackers will provide the decryption key or that the….

