Often overlooked, IT asset and inventory management is crucial data for businesses to properly maintain. In an era where cyber threats are increasingly sophisticated and pervasive, the need for robust IT asset and inventory management has never been more critical. Effective asset management goes beyond mere record-keeping; it is a foundational practice that enhances security,….
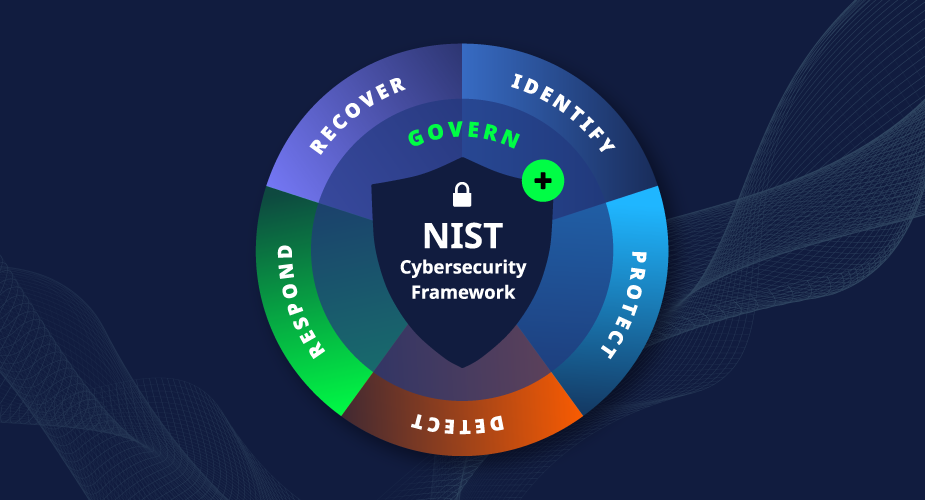
Improve Cyber Hygiene in 2024: Make A New Year’s Resolution to align with NIST Cybersecurity Framework
2024 is a great time for business owners and executives to be aware of the investments that the federal government has made to help businesses with cybersecurity best practice initiatives. For those not paying close attention there is a particular organization – the National Institute of Standards and Technology (NIST). NIST first produced their Cybersecurity….

The Evolving Threat of Hacking: Protecting Your Business in 2024
The Escalation of Cyber Attacks Over the past few years, the frequency and sophistication of cyber-attacks have escalated dramatically. Cybersecurity leaders acknowledge that cyberattacks are increasing and they expect prevalence of attempts to continue to increase over the foreseeable future. In the past 18-months there has been a staggering increase in phishing attacks reported with….

October Cybersecurity Awareness Announcement: Employee Training is Non-Negotiable!
In the world of cybersecurity, October is more than just the onset of autumn; it’s Cybersecurity Awareness Month. Declared as such by some anonymous “powers that be,” this month serves as a vital reminder of the critical role each one of us plays in protecting the digital landscapes of our organizations. But, there’s a harsh….

Navigating the Spectrum: Exploring the Three Flavors of Outsourced IT Service Providers
The following depiction is used as an oversimplification of the market to help you visualize the types of service providers offering outsourced IT Services. This generalization is based on our opinions and knowledge of the market for what we often call “Managed IT Services”. In greater Pittsburgh alone there are likely over 100 outfits to….

