In cybersecurity, lateral movement refers to techniques used by attackers to move within a network after initially compromising a single system. This can include techniques such as using stolen credentials to access other systems, exploiting vulnerabilities in network infrastructure, and using remote administration tools. The goal of lateral movement is typically to gain access to sensitive data or to maintain a foothold in the network for future attacks.
Lateral movement is commonly identified by cyber security solutions that can ingest East-West network traffic for analysis, not just North-South network traffic. East-West monitoring for lateral movement is important because it allows organizations to detect and respond to malicious activity that occurs within the internal network. This contrasts with North-South monitoring, which primarily focuses on only detecting and preventing external threats from entering the network through the firewall.
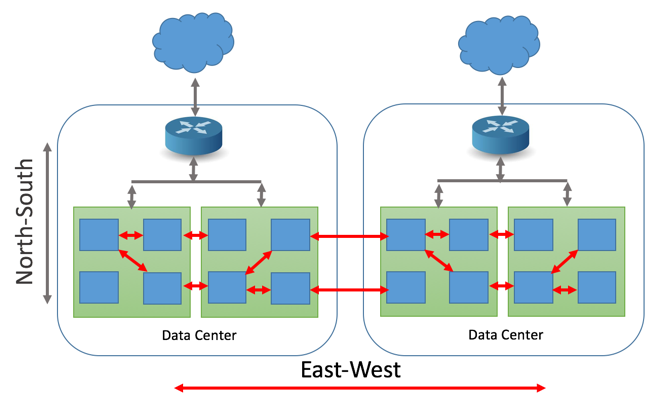
East-West traffic refers to the communication between different systems and services within a network. This type of traffic is typically considered less risky than North-South traffic, which is the communication between a network and external networks, such as the internet. However, once an attacker has compromised a system within a network, they can use East-West traffic to move laterally and gain access to sensitive data or other systems.
By monitoring East-West traffic, organizations can detect unusual patterns of activity that could indicate an attacker is attempting to move laterally. This could include, for example, an attacker attempting to connect to a large number of systems within a short period of time or attempting to connect to systems that they do not normally access. By detecting this type of activity, organizations can take steps to prevent the attacker from achieving their objectives and limit the scope of the attack.
East-West monitoring is also important because it can help organizations identify and respond to attacks that may have bypassed traditional perimeter security measures. For example, attackers may be able to gain access to a network through a legitimate user account, or by exploiting a vulnerability in a system or application that is not properly configured. By monitoring East-West traffic, organizations can detect these types of attacks and take steps to contain them.
Here are several ways to help limit lateral movement, as well as some approaches to monitoring for lateral movement in your infrastructure:
- Network segmentation: By segmenting a network into smaller, separate segments, it becomes more difficult for attackers to move laterally.
- Log monitoring: By monitoring system and network logs, it is possible to detect unusual patterns of activity that could indicate an attacker is attempting to move laterally.
- Intrusion detection and prevention systems (IDPS): These systems can detect and prevent lateral movement by analyzing network traffic for malicious patterns.
- Endpoint detection and response (EDR) tools: These tools monitor the activity on individual systems and can detect and respond to malicious activity.
- User behavior analytics (UBA): These systems use machine learning to analyze user behavior and detect anomalies that could indicate an attacker is attempting to move laterally.
- Security information and event management (SIEM) systems: These systems aggregate and analyze log data from multiple sources to detect and respond to security incidents.
- Network access control (NAC): This technology can identify and authenticate users and devices on the network and prevent unauthorized access.
- Deception technology: This technology creates fake data, credentials, or systems to distract the attacker from the real target and detects the attacker’s activity.
It is important to note that monitoring for lateral movement should be part of a comprehensive security strategy that includes both preventative and detective controls as security is best approached by implementing layers of protection.
Advanticom believes that each of the above recommendations will enhance your organization’s cybersecurity posture. However, if you are just starting to invest in improving your protection and detection capabilities the best thing you can do is begin to accumulate data to give yourself the ability to analyze East-West traffic within your network. This can be achieved by first implementing a best-in-class EDR tool and then the next step is to aggregate that data with the rest of your network activity into a SIEM platform. If you do not have an in-house SOC, both of these solutions should be outsourced to a qualified partner that operates 24/7 and has security expertise on staff to extract value from the collected data.


