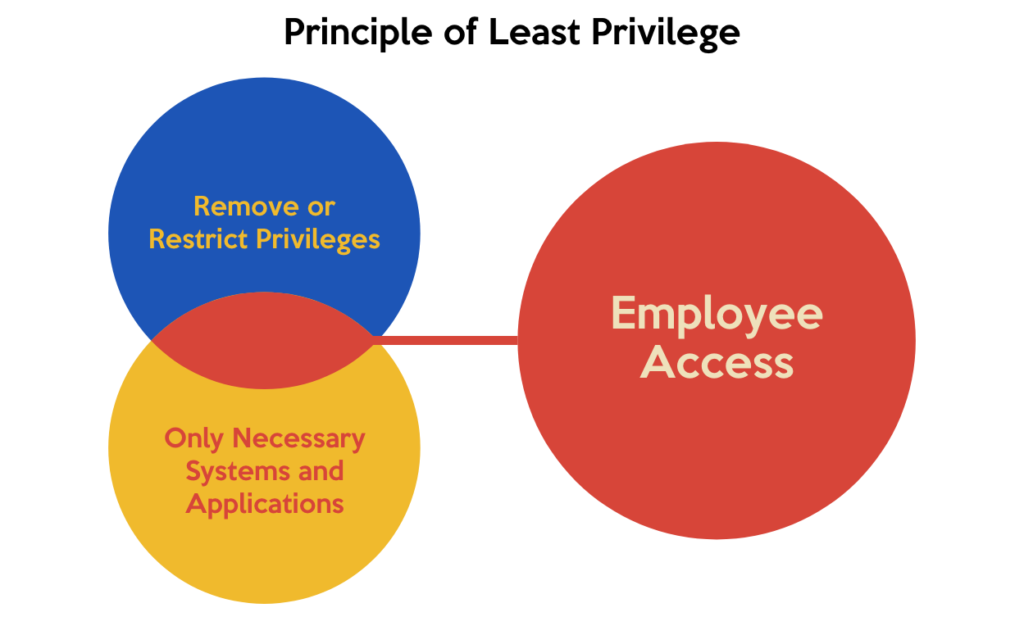
The principle of Least Privilege (POLP), also known as the principle of least authority or least access, is a security concept in computer systems and networks that limits the access rights of users and programs to the bare minimum necessary to perform their tasks.
The principle of least privilege is considered a fundamental principle of IT security as well as a key component for defense-in-depth strategies. By limiting the attack surface of a system, it makes it harder for attackers to compromise the system and steal sensitive data or disrupt operations.
In practice, this means that users are granted only the necessary permissions to perform their jobs, and no more. This minimizes the damage that can be done in the event of a security breach, as attackers will have limited access to sensitive data or systems.
For example, an employee in a company’s finance department may require access to financial records and payment systems, but they do not need access to the company’s marketing materials or customer data. By limiting their access to only the systems and data they need to do their job, the risk of unauthorized access or accidental data leak is reduced.
Similarly, computer programs and software are also given only the necessary permissions to run properly. If a program does not need to access certain files or settings, those permissions are not granted, reducing the potential attack surface of the system. This approach is in alignment with network segmentation and grouping resources togather that need to communicate and segmenting other systems that do not need to communicate with other systems.
The referenced examples are very common across many organizations that follow best practices for good cyber hygiene. But who is keeping an eye on the IT admins or outsourced IT vendors that are responsible for managing the permissions for principle of least privilege? It’s just as important for the IT admins and outsourced vendors to also follow best practices when it comes to POLP. Here is some insight on how an internal IT team or outsourced IT partners should handle their own accounts as it relates to the principle of least privileged.
IT administrators should have separate and individually named admin accounts for several reasons, including but not limited to:
- Security: Using a separate admin account can help prevent unauthorized access to sensitive information or system resources. Admin accounts typically have higher privileges and access to more resources than regular user accounts, so having a separate account with these privileges can help prevent accidental or intentional misuse of these permissions.
- Accountability: When multiple administrators share the same admin account, it can be difficult to determine who made changes or accessed certain resources. By having separate admin accounts for each administrator, it’s easier to track activity and hold individuals accountable for their actions.
- Auditing and compliance: Many compliance frameworks and regulations require companies to have detailed logs of system activity and user actions. By using separate admin accounts, it’s easier to create and maintain detailed logs of system activity, which can be used for auditing and compliance purposes.
- Separation of duties: Separating admin accounts can help enforce the principle of least privilege and separation of duties, which are important security principles. By separating the duties of system administration, it reduces the risk of accidental or intentional misuse of system privileges.
Overall, Advanticom believes having separate admin accounts is an important security best practice that helps reduce the risk of unauthorized access, improve accountability and compliance, and enforce separation of duties when used in conjunction with the principles of least privileges.

Every organization should consider their specific circumstances and take action to reduce risk. If you need help identifying and mitigating the risks in your organization the team at Advanticom can help to evaluate solutions. Please reach out to the Advanticom team to discuss your ideas or ask questions at ATeam@advanticom.com.