2024 is a great time for business owners and executives to be aware of the investments that the federal government has made to help businesses with cybersecurity best practice initiatives. For those not paying close attention there is a particular organization – the National Institute of Standards and Technology (NIST). NIST first produced their Cybersecurity Framework (CSF) in 2014 which is a set of guidelines and best practices designed to help organizations manage and improve their cybersecurity posture. NIST CSF provides a framework that organizations of all sizes and across various industries can use to assess and strengthen their cybersecurity efforts to effectively manage cybersecurity risks.
If you haven’t heard of NIST CSF before you’ve probably overlooked it. Compliance frameworks aren’t sexy and standardization, best practices, and continuous improvement sound like process jargon from a bad Organization Behavioral class in your undergraduate studies, but there is real value to pay attention to here. NIST has existed in different forms for over 100 years with the purpose of helping American industry track and adapt to changing technologies. NIST CSF was created to as a benchmark of best practices businesses can follow to improve cybersecurity posture, but even furthermore NIST CSF is a standard of practices that if businesses follow will protect industry as a whole and the national security of our economy. Aligning to NIST CSF will be an improvement in your organization’s cyber posture and an enhancement that helps to guaranteed our economic future. Aligning to NIST CSF means you are taking a proactive approach to cybersecurity which is a strategic investment in the long-term success and security of your business.
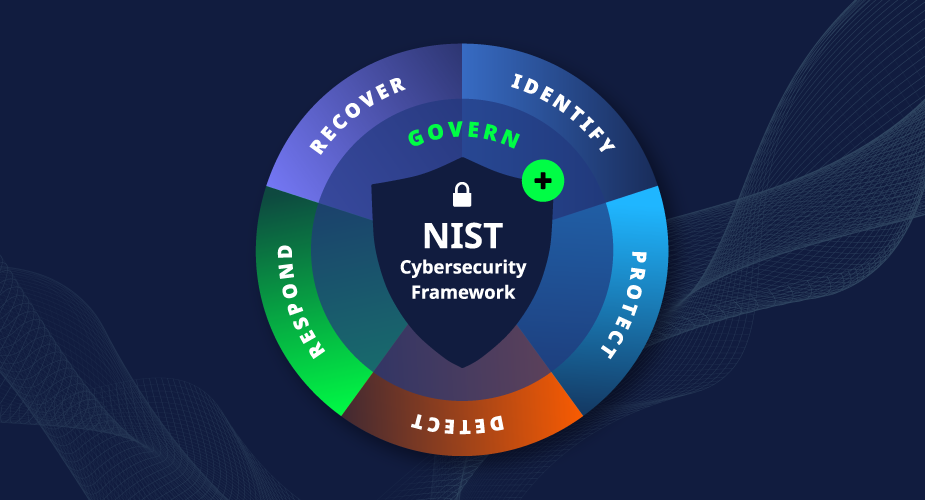
In the dynamic world of technology, the National Institute of Standards and Technology Cybersecurity Framework offers a comprehensive approach to managing and mitigating cyber risks. NIST CSF consists of five pillars: Identify, Protect, Detect, Respond, and Recover.
- Identify:
- Description: The Identify function focuses on understanding and managing cybersecurity risks to systems, assets, data, and capabilities. This involves identifying, documenting, and categorizing information to provide a foundation for effective cybersecurity management.
- Key Activities:
- Asset Management: Identifying and managing all assets within the organization.
- Business Environment: Understanding the organizational context, priorities, and risk tolerance.
- Risk Assessment: Conducting assessments to identify and prioritize cybersecurity risks.
- Protect:
- Description: The Protect function is concerned with implementing safeguards and measures to ensure the delivery of critical services and the protection of assets. It involves the development and implementation of security policies, procedures, training and controls.
- Key Activities:
- Access Control: Ensuring that only authorized individuals have access to systems and data.
- Data Security: Implementing measures to protect data throughout its lifecycle.
- Training and Awareness: Providing cybersecurity training to employees and promoting awareness of security best practices.
- Detect:
- Description: The Detect function involves the establishment of mechanisms to identify and detect cybersecurity events. The goal is to promptly discover any anomalies or security incidents that may compromise the organization’s systems or data.
- Key Activities:
- Continuous Monitoring: Implementing continuous monitoring processes to detect cybersecurity events in real time.
- Anomaly Detection: Identifying unusual patterns or behaviors that may indicate a security incident.
- Incident Detection and Response: Developing capabilities to detect and respond to cybersecurity incidents.
- Respond:
- Description: The Respond function is focused on developing and implementing an effective incident response plan. It aims to ensure that the organization can respond promptly and efficiently to a cybersecurity incident, minimizing the impact on business operations with recovery strategies that are already in place.
- Key Activities:
- Incident Response Planning: Developing and implementing an incident response plan.
- Communication: Establishing communication plans for internal and external stakeholders.
- Mitigation: Taking immediate actions to contain and mitigate the impact of a cybersecurity incident.
- Recover:
- Description: The Recover function addresses the organization’s ability to restore and recover capabilities or services that were impaired due to a cybersecurity incident. It involves planning for resilience and learning from incidents to improve future response efforts.
- Key Activities:
- Recovery Planning: Developing and implementing plans for the recovery of systems and data.
- Improvements: Analyzing incidents to identify areas for improvement and implementing changes.
- Communication: Keeping stakeholders informed about recovery efforts and progress.
NIST CSF provides companies with a comprehensive approach and framework to approach cybersecurity. The framework enables businesses to leverage a structured system to identify, analyze, and manage risk so each business can reduce the risk of a major cyber incident and reduce the impact that any such breach would have.
In 2024 make it a New Year’s Resolution to plan the implementation of NIST CSF into your own IT operations. By doing so, you commit to enhancing your cyber hygiene, fortifying your defenses against evolving threats, and demonstrating a proactive approach to cybersecurity. In an era where digital resilience is paramount, embracing the NIST framework is a strategic investment in the long-term success and security of your business.

At Advanticom as we bid farewell to the challenges and triumphs of the past year we are focusing our organization on helping our clients become more secure and cyber resilient. Frameworks like NIST CSF continue to help businesses navigate the ever-changing cybersecurity landscape and we know investing in the framework helps businesses continue to invest in a proactive stance against cyber threats ensuring a secure and prosperous future for their organization. Advanticom offers our clients support in aligning their IT operations to NIST CSF to improve cyber resiliency. If you are looking for guidance please reach out and we will be happy to assist.