The Escalation of Cyber Attacks Over the past few years, the frequency and sophistication of cyber-attacks have escalated dramatically. Cybersecurity leaders acknowledge that cyberattacks are increasing and they expect prevalence of attempts to continue to increase over the foreseeable future. In the past 18-months there has been a staggering increase in phishing attacks reported with….

October Cybersecurity Awareness Announcement: Employee Training is Non-Negotiable!
In the world of cybersecurity, October is more than just the onset of autumn; it’s Cybersecurity Awareness Month. Declared as such by some anonymous “powers that be,” this month serves as a vital reminder of the critical role each one of us plays in protecting the digital landscapes of our organizations. But, there’s a harsh….

Building Resilience: The Importance of Business Continuity Planning
As the saying goes, “Hope for the best, but prepare for the worst.” That’s exactly what a business continuity plan (BCP) does – it helps organizations prepare for unexpected disruptions that could threaten their operations and profitability. While the idea of creating a BCP may seem daunting, the truth is that it’s an essential step….
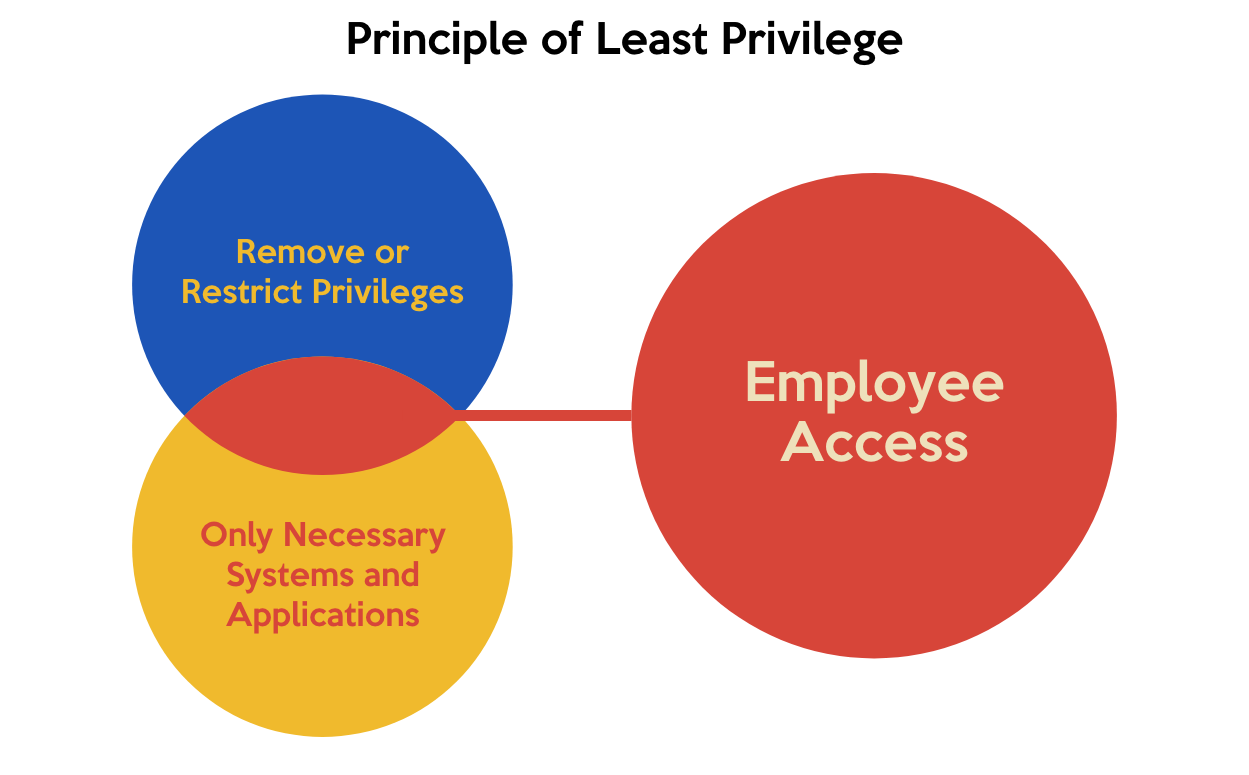
The Principle of Least Privilege
The principle of Least Privilege (POLP), also known as the principle of least authority or least access, is a security concept in computer systems and networks that limits the access rights of users and programs to the bare minimum necessary to perform their tasks. The principle of least privilege is considered a fundamental principle of….
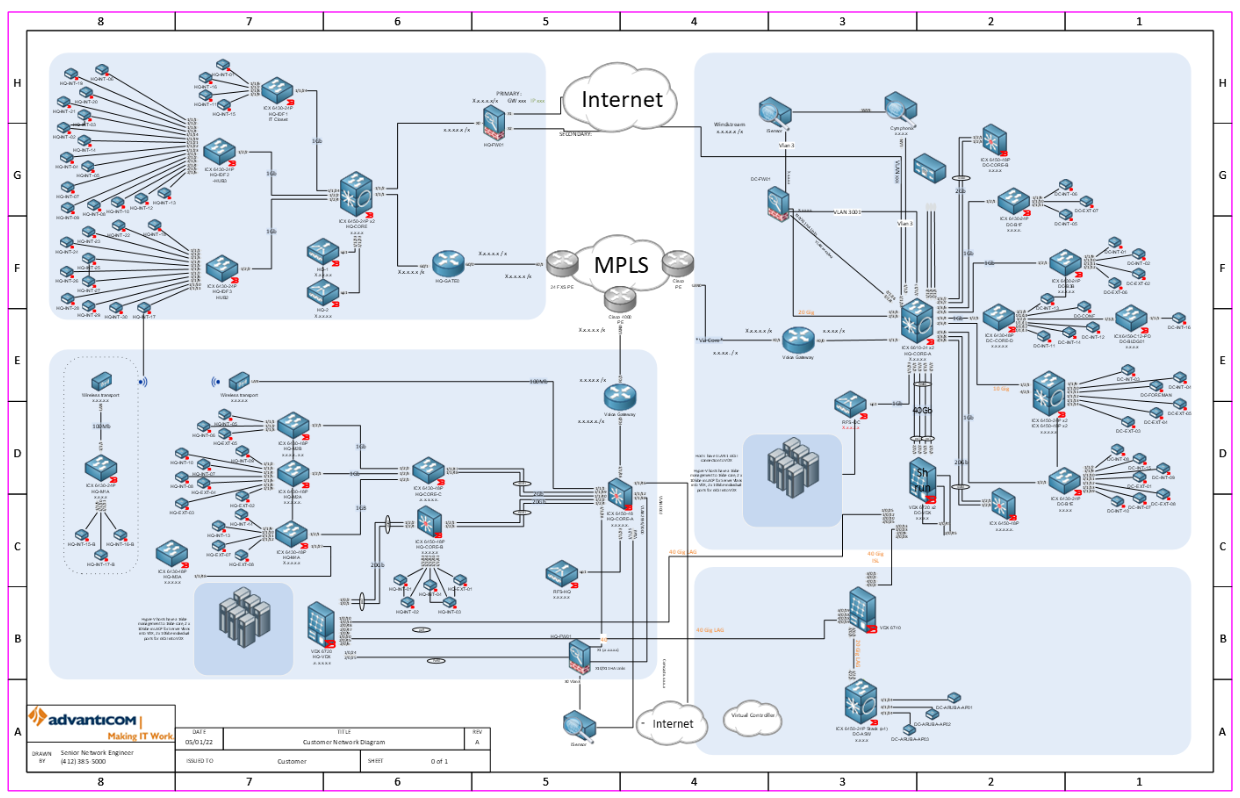
The Importance of Network Documentation
The intended audience of this blog includes business owners, executives, IT managers, IT engineers and those curiously interested in IT. We seek to provide you with the latest IT knowledge and insights from our behind-the-scenes experience. We provide this information to help you manage the specific costs and risks of IT in your business. You have heard it many times before: maintaining proper documentation is critical to your organization. It provides a….

